Security
Get A+ scores on Mozilla Observatory out of the box. Easily change the default Security Headers to suit your needs.
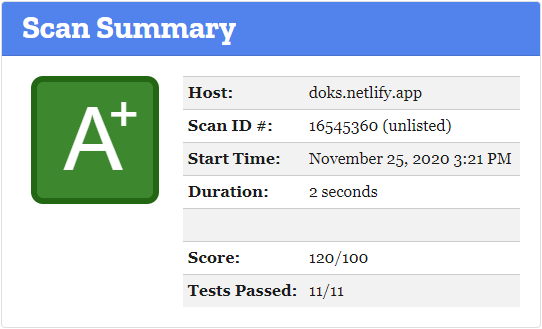
See also Mozilla Observatory: Scan Results for doks.netlify.app
Netlify
See also the Netlify website: Security at Netlify.
Security Headers
./layouts/index.headers excerpt:
/*
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'none'; manifest-src 'self'; connect-src 'self'; font-src 'self'; img-src 'self'; script-src 'self'; style-src 'self'
X-Frame-Options: SAMEORIGIN
Referrer-Policy: strict-origin
See also: Headers.
Content Security Policy
Subresource Integrity
Subresource Integrity is applied to Doks CSS and JS files when building your Doks site for production (and other non development sites):
./layouts/partials/head/stylesheet.html./layouts/partials/footer/script-footer.html
See also the Hugo Docs: Fingerprinting and SRI.
Doks Codebase
The Doks Codebase is regularly checked for vulnarabilites with an automated CodeQL workflow.
See also the GitHub docs: Finding security vulnerabilities and errors in your code
Dok Dependencies
The Doks Dependencies are regularly checked for updates with an automated Dependabot process.
See also the GitHub docs: Keeping your dependencies updated automatically